The Limits of Transaction-Centric Fraud Detection
Financial institutions today operate in an environment defined by relentless transaction velocity, always-on digital channels, and increasingly organised fraud ecosystems.
Payment rails that once processed thousands of transactions per second now routinely handle volumes several orders of magnitude higher, while customer expectations for speed and availability continue to rise.
Despite this shift, most fraud detection systems remain anchored to a legacy assumption: that fraud can be identified by analysing individual transactions in isolation.
This assumption no longer holds.
Modern fraud does not occur as a series of unrelated anomalies. It manifests as coordinated behaviour across multiple entities, accounts, and time windows.
When detection systems remain transaction-bound, they inevitably miss the broader structure within which fraud operates.
The result is delayed detection, excessive false positives, and a growing gap between how fraud behaves and how it is monitored.
IDYC360 addresses this gap by reframing fraud detection around networks, not transactions.
Its proprietary Payer & Beneficiary Tracking Network exemplifies this shift, transforming raw transaction data into real-time behavioural intelligence.
Why Transactions Alone No Longer Tell the Full Story
Traditional fraud controls are optimised to answer narrow questions: Is this transaction unusual?
Does it breach a predefined rule? Does it resemble a known pattern?
While such checks remain useful, they are inherently reactive. They detect symptoms rather than structures.
Fraud networks exploit this limitation by distributing activity across multiple entities, rotating identities, and maintaining transaction values below alert thresholds. Individually, each transaction appears benign.
Collectively, they form a coherent and deliberate pattern.
The real signal, therefore, lies not in the transaction itself, but in the relationships between participants.
Understanding who transacts with whom, how frequently, in what structural configurations, and how those configurations evolve is now essential.
This requires moving beyond linear analysis into continuous relationship mapping, which is precisely the problem IDYC360’s network intelligence is designed to solve.
Introducing the Payer & Beneficiary Tracking Network
The Payer & Beneficiary Tracking Network is a live, graph-based intelligence layer that continuously models transactional relationships across a financial institution’s ecosystem.
Instead of treating payments as isolated events, the network represents:
- Entities as nodes
- Transactional relationships as edges
- Behavioural evolution as changes in network structure
This approach allows IDYC360 to observe not only activity, but interaction, coordination, and role dynamics.
Crucially, the network is not static. It is updated in real-time, with every transaction contributing to the evolving behavioral context of both payers and beneficiaries.
This ensures that intelligence remains current, continuous, and resistant to evasion tactics that rely on timing gaps or fragmented visibility.
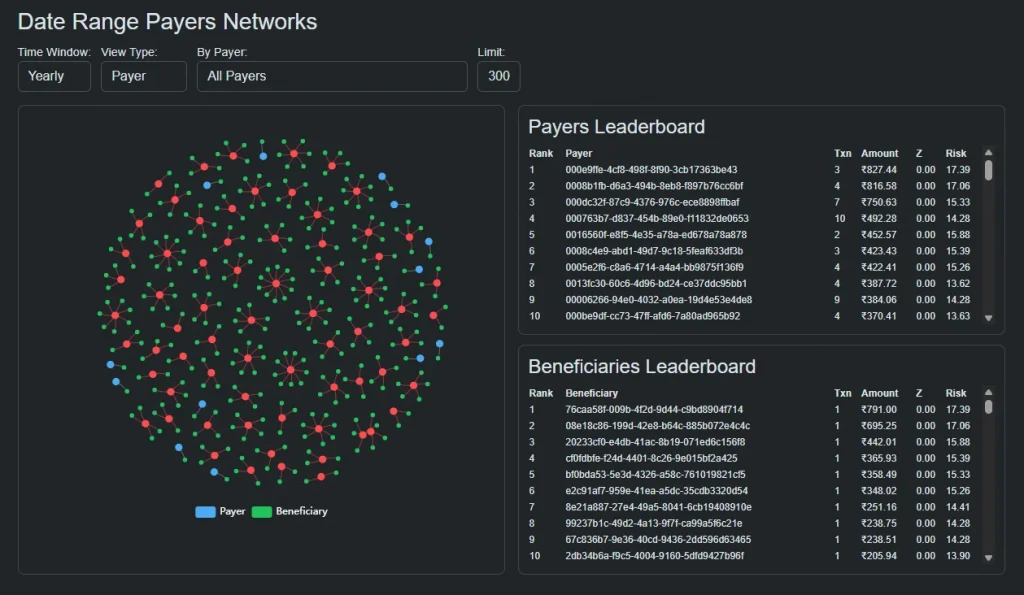
Payer-Centric Intelligence: Understanding Risk at the Source
The payer-focused view of the network examines how funds originate and propagate through the system.
This perspective is particularly effective for identifying upstream fraud behaviours that initiate financial crime.
In this view, risk emerges not from a single transaction, but from patterns of payer behaviour over time.
Payers that interact with an unusually broad or changing set of beneficiaries, or that mirror the behaviour of other high-risk payers, begin to stand out structurally even when individual payments appear ordinary.
Such patterns are difficult to detect using rule-based or transaction-scoring approaches because they rely on continuity rather than thresholds.
By contrast, network intelligence identifies consistency in behaviour, topology, and interaction patterns.
This enables early detection of fraud typologies such as coordinated mule deployment, account takeover-driven disbursements, and distributed probing attacks.
Instead of reacting after damage has occurred, IDYC360 allows institutions to intervene while risk is still forming.
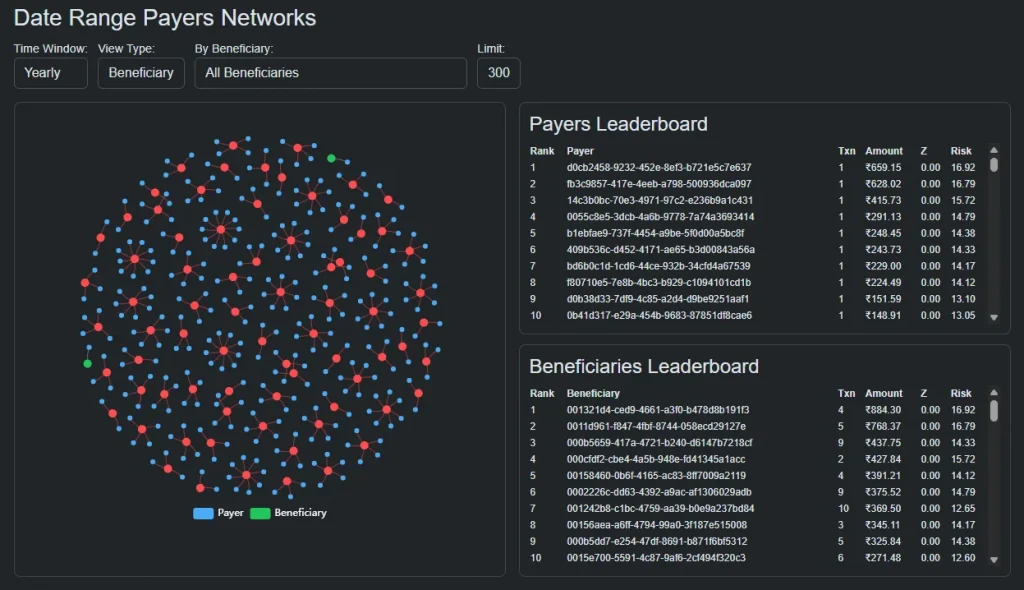
Beneficiary-Centric Intelligence: Revealing Where Risk Converges
While payer analysis addresses where risk originates, beneficiary-centric intelligence reveals where it consolidates.
The beneficiary-focused network view highlights entities that receive funds from multiple, often unrelated, payers.
In many fraud typologies, beneficiaries are deliberately stabilised while payer identities are rotated.
This allows networks to persist even as individual accounts are flagged or shut down.
By shifting the analytical lens to beneficiaries, IDYC360 highlights structural risks that transaction-centric systems often overlook.
Beneficiaries with low transaction counts but unusually diverse payer relationships can be just as risky as high-volume actors.
In fact, such profiles are often more indicative of laundering or aggregation behaviour.
This view also reveals asymmetric transaction flows, where inbound activity significantly outweighs outbound movement.
These imbalances are strong indicators of mule accounts or intermediate layering nodes within broader financial crime networks.
The Importance of Dual-Lens Network Analysis
Fraud networks are inherently adaptive.
Entities change roles, transaction patterns evolve, and surface-level indicators are deliberately manipulated to evade detection.
A system that observes only one side of the transaction equation inevitably develops blind spots.
IDYC360 eliminates these blind spots by enabling seamless pivoting between payer-centric and beneficiary-centric views.
This dual-lens approach allows investigators and risk engines alike to:
- Cross-validate behavioural signals across roles
- Identify role fluidity within fraud networks
- Detect structural consistency even as transaction details vary
- Build a more complete picture of network intent
Rather than producing isolated alerts, the system constructs an evolving map of financial relationships, enabling higher-confidence decisions with fewer false positives.
Real-Time Network Intelligence Enabled by FPSM
Network intelligence is only effective if it operates at transaction speed. Delayed aggregation or batch processing undermines the very behaviours fraudsters exploit.
IDYC360’s Fraud Pattern Speed Matching (FPSM) architecture ensures that network evaluation occurs continuously, without time-slice gaps or deferred decision queues.
Every transaction updates the network state immediately, preserving behavioural continuity across events.
This capability is critical in high-velocity environments where milliseconds matter. Fraud often exploits micro-delays between systems or monitoring stages.
By eliminating these gaps, IDYC360 ensures there is no safe window for coordinated abuse.
Predictive Intelligence Instead of Reactive Alerts
Most fraud systems alert when predefined conditions are met. IDYC360 predicts when risk trajectories are forming.
Its multi-layer machine learning pipeline continuously adapts to behavioural changes, ensuring that detection logic evolves alongside attacker tactics.
Sliding feature windows capture gradual shifts in network behaviour, while real-time inference ensures decisions remain context-aware.
The Payer & Beneficiary Tracking Network thus functions as a predictive intelligence surface, not a reporting tool. It does not merely describe what has happened; it anticipates what is likely to happen next.
Governance, Explainability & Regulatory Confidence
Advanced fraud detection must be explainable to be operationally viable and regulatorily defensible.
Network-based intelligence naturally supports explainability by tying risk decisions to observable relationships and behaviours.
When an entity is flagged, investigators can see not just a score, but the network context that produced it.
This enables:
- Clear articulation of why the risk was identified
- Visual and structural evidence for investigative decisions
- Reconstruction of historical risk evolution
- Audit-ready documentation without manual effort
For compliance and audit teams, this transforms fraud detection from a black box into a transparent control framework.
Privacy-by-Design Deployment Model
Despite its analytical depth, IDYC360’s network intelligence does not compromise data governance.
The platform operates entirely within the institution’s infrastructure, with no external data custody or retention. All intelligence is generated in place, under client-controlled security and governance frameworks.
This ensures that institutions can deploy advanced fraud detection without introducing new privacy, residency, or regulatory risks.
Strategic Value for Financial Institutions
By shifting fraud detection from transactions to networks, IDYC360 enables institutions to regain control over complexity.
Key strategic outcomes include:
- Earlier detection of organised fraud activity
- Reduced false positives through contextual intelligence
- Improved investigator efficiency and prioritisation
- Stronger governance and audit confidence
- Greater resilience in high-velocity payment ecosystems
Rather than scaling alerts, institutions scale understanding.
Fraud Is Networked; Detection Must Be Too
Fraud has evolved into a coordinated, adaptive, and network-driven threat. Detection approaches that remain transaction-centric will continue to lag behind the attacker sophistication.
IDYC360’s Payer & Beneficiary Tracking Network demonstrates that effective fraud detection is no longer about spotting anomalies in isolation. It is about understanding relationships, behaviour, and structure in real time.
In high-velocity financial ecosystems, resilience is defined by intelligence, speed, and continuity.
Ready to Stay
Compliant—Without Slowing Down?
Move at crypto speed without losing sight of your regulatory obligations.
With IDYC360, you can scale securely, onboard instantly, and monitor risk in real time—without the friction.